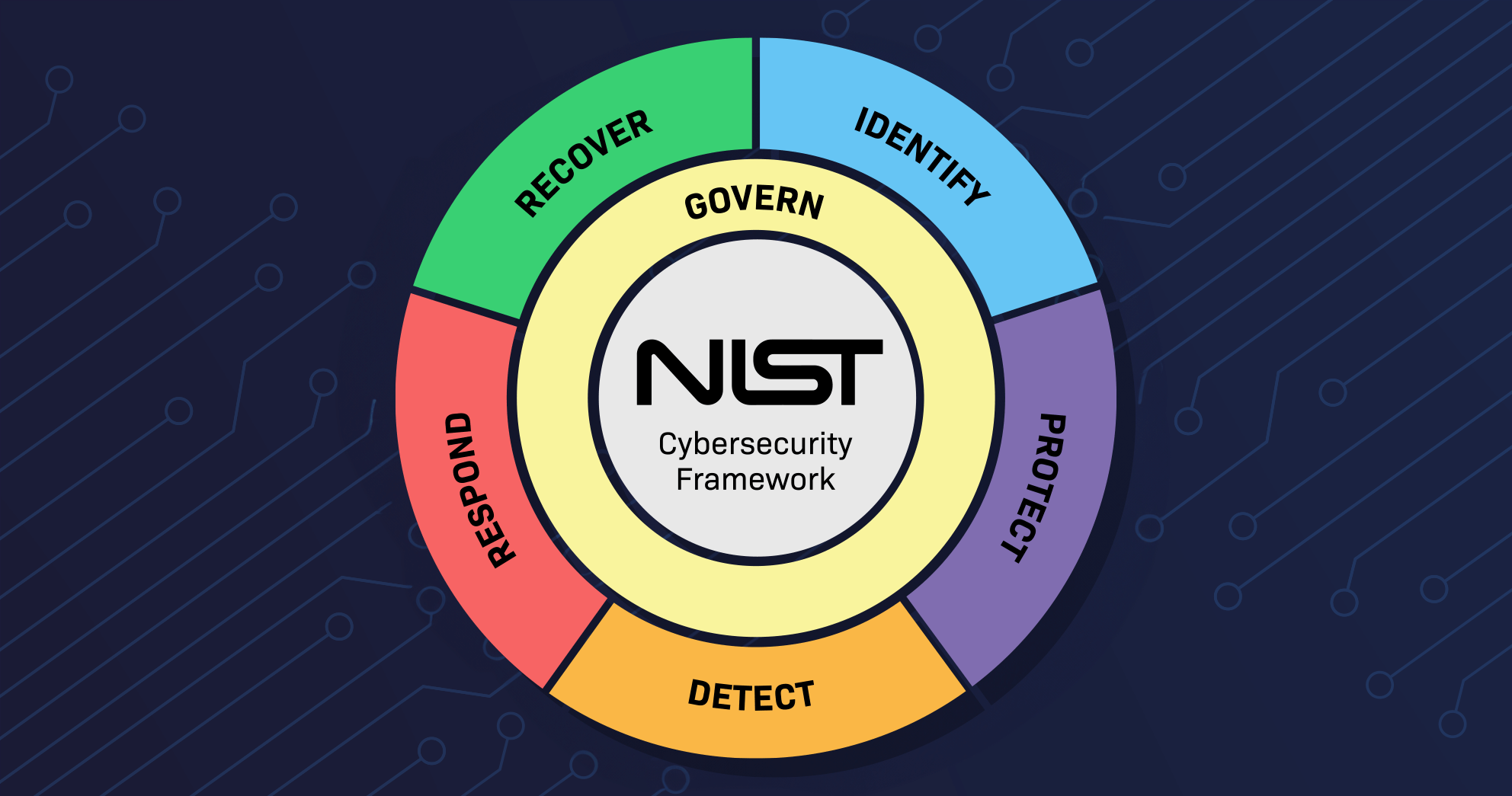
The NIST Cybersecurity Framework (CSF) 2.0 introduces several enhancements to help organizations manage their cybersecurity risks better. One of the most significant updates is the refined approach to Organizational Profiles. These Profiles are essential for understanding an organization’s cybersecurity posture, setting target objectives, and tracking progress over time.
This step-by-step guide will walk you through the process of creating and using Organizational Profiles in NIST CSF 2.0, ensuring that your cybersecurity strategy is aligned with your overall business objectives.
In my last article, I shared why NIST CSF is a valuable business tool for leadership and some key opportunities to improve the new 2.0 framework.
View my latest articles about NIST CSF.
You can connect with me on LinkedIn and join my professional network.
I share weekly insights on quantifying cyber risk in dollars, not colors — including Monte Carlo simulation, loss exceedance modeling, Cyber Value at Risk (VaR), and NIST CSF quantification. If you’re an executive, CISO, or security leader looking for practical, data-driven approaches to cyber risk, let’s connect on LinkedIn.

Step 1: Define the Scope of Your Organizational Profile
Before creating an Organizational Profile, you need to determine its scope. This involves identifying the areas of your organization that the Profile will cover. The scope can vary depending on your organization’s needs, ranging from the entire organization to specific divisions, assets, or types of threats.
Key Questions to Consider:
- What is the purpose of this Organizational Profile?
- Will the Profile cover the entire organization or only specific parts?
- What types of cybersecurity threats, vulnerabilities, and defenses will be included?
- Who will be responsible for developing, reviewing, and maintaining the Profile?
Example: A financial institution might create separate Organizational Profiles for its online banking platform, internal financial systems, and third-party vendor management.
It is common and also recommended for organizations to create various differnt profiles.
Step 2: Gather Necessary Information
Once the scope is defined, the next step is to gather all relevant information that will inform your Organizational Profile. This includes existing policies, risk management priorities, cybersecurity requirements, and any relevant standards or frameworks your organization follows.
Sources of Information May Include:
- Internal cybersecurity policies and procedures
- Results from previous risk assessments
- Current threat intelligence and vulnerability data
- Industry standards and regulatory requirements
- Stakeholder expectations and mission objectives
Example: For a healthcare organization, this step might involve gathering information on HIPAA compliance, recent security audits, and patient data protection policies.
Ready to elevate your cybersecurity strategy with a data-driven approach?
Schedule a time with me to discuss your specific NIST CSF 2.0 risk assessment needs. I’ll provide tailored insights and professional recommendations on how a quantitative approach can give you clearer, more actionable results to strengthen your cybersecurity posture.
Step 3: Create the Organizational Profile
With the information in hand, you can begin creating the Organizational Profile. The NIST CSF 2.0 provides a template that can be customized to suit your organization’s specific needs. The Profile should include a detailed description of the cybersecurity outcomes your organization is currently achieving (Current Profile) and the desired outcomes you aim to achieve (Target Profile).
Steps to Follow:
- Download and customize the NIST CSF Organizational Profile template: Adjust the template to reflect the scope and specific needs of your organization.
- Document Current Practices: Describe the current state of your cybersecurity practices for each relevant CSF outcome.
- Set Target Outcomes: Define the goals you wish to achieve, based on strategic objectives, anticipated threats, and new technologies.
- Assign Priorities: Use the template’s priority field to indicate the relative importance of each goal.
Example: A retail company might document that its current access control practices are partially implemented (Current Profile) and set a target of fully automating access controls with multi-factor authentication (Target Profile).
Step 4: Analyze Gaps and Develop an Action Plan
Once both the Current and Target Profiles are complete, the next step is to perform a gap analysis. This process involves comparing the current state of your cybersecurity practices with your desired outcomes, identifying areas where improvements are needed.
Steps to Perform Gap Analysis:
- Identify Gaps: Highlight the differences between current practices and target outcomes.
- Prioritize Improvements: Determine which gaps are most critical to address based on risk impact, compliance requirements, and organizational priorities.
- Develop an Action Plan: Create a detailed plan to address each gap, including timelines, resources needed, and responsible parties.
Example: If the gap analysis reveals that incident response plans are outdated, the action plan might include updating the response protocols, conducting staff training, and testing the revised plans through simulated exercises.
Step 5: Implement the Action Plan and Monitor Progress
After developing the action plan, the next step is implementation. This involves deploying the necessary changes to meet your target outcomes and continuously monitoring progress.
Steps for Implementation:
- Assign Responsibilities: Ensure that all tasks in the action plan have clear ownership and deadlines.
- Deploy Controls: Implement technical, administrative, and physical controls as outlined in the action plan.
- Monitor Key Performance Indicators (KPIs): Track the effectiveness of the changes using relevant KPIs and Key Risk Indicators (KRIs).
- Update Profiles: As improvements are made, update the Organizational Profile to reflect the new cybersecurity posture.
Example: A manufacturing firm might implement new network segmentation controls and monitor network traffic to ensure that the changes reduce the risk of cyber attacks on critical production systems.
Step 6: Review and Update the Organizational Profile Regularly
Cybersecurity is a dynamic field, and an organization’s risk environment can change rapidly. It is important to regularly review and update your Organizational Profile to ensure it remains relevant and effective.
Best Practices for Ongoing Review:
- Regular Assessments: Conduct periodic reviews of your Current and Target Profiles to assess progress and identify new risks.
- Incorporate Feedback: Use insights from incident reports, audits, and stakeholder feedback to refine your Profiles.
- Adapt to Changes: Update the Profiles to reflect changes in the threat landscape, regulatory environment, and business objectives.
Example: A technology company might update its Organizational Profile quarterly to reflect new software vulnerabilities or changes in data protection regulations.
Conclusion
Implementing Organizational Profiles in NIST CSF 2.0 is a structured process that helps organizations align their cybersecurity efforts with business goals, manage risks more effectively, and track progress over time. By following the steps outlined in this guide, you can create and maintain a comprehensive cybersecurity posture that adapts to the evolving digital landscape.
Regularly updating your Profiles ensures that your organization remains resilient against emerging threats and can continue to protect its critical assets and operations. As cybersecurity challenges become more complex, the ability to strategically manage and communicate risk becomes increasingly important, making Organizational Profiles an invaluable tool in your cybersecurity arsenal.
Enhancing the NIST CSF 2.0 Framework: Integrating Probabilistic Risk Quantification for Greater Impact

The NIST Cybersecurity Framework (CSF) 2.0 has made significant strides in helping organizations manage and reduce cybersecurity risks. Its clear structure and focus on aligning cybersecurity efforts with business objectives has become an essential tool for many industries.
However, as the threat landscape evolves, there are opportunities to further enhance the effectiveness and applicability of the NIST CSF. One of the most promising areas for improvement is the integration of probabilistic risk quantification into the framework. This approach can help organizations better prioritize risks, make informed decisions about cybersecurity investments, and communicate cyber risk in economic terms, thereby increasing the framework’s overall value.
I created a free comprehensive primer on Bayes’ Theorem for Cybersecurity Risk Analysis that illustrates some of the important concepts I share in the sections below. You will learn the foundational concepts of Bayesian statistics and how to apply them effectively in the context of cybersecurity.
You can connect with me on LinkedIn and join my professional network.
The Business Case for Probabilistic Risk Quantification
Traditional risk assessment methods often rely on qualitative or semi-quantitative approaches, which can be subjective and lack precision. These methods typically involve categorizing risks as “high,” “medium,” or “low” based on expert judgment or historical data. While useful, these approaches can fall short in providing the detailed insights needed for making informed decisions about where to allocate resources effectively.
Probabilistic risk quantification, on the other hand, offers a more rigorous and data-driven approach. By leveraging statistical methods and models, organizations can quantify the likelihood of various cyber threats and the potential impact of these threats in economic terms. This approach allows for a more nuanced understanding of risk, enabling organizations to prioritize their cybersecurity efforts based on the actual probability of an event occurring and the potential financial consequences.
If you are interested in exploring cyber risk quantification, follow my blog at https://timlayton.blog, and you will have the opportunity to be notified when I publish new articles and white papers.
I share weekly insights on quantifying cyber risk in dollars, not colors — including Monte Carlo simulation, loss exceedance modeling, Cyber Value at Risk (VaR), and NIST CSF quantification. If you’re an executive, CISO, or security leader looking for practical, data-driven approaches to cyber risk, let’s connect on LinkedIn.
Enhancing Risk Prioritization
One of the primary benefits of integrating probabilistic risk quantification into the NIST CSF 2.0 framework is the ability to prioritize risks more effectively. In a world where resources are limited, organizations need to focus on the threats that pose the greatest risk to their operations.
For example, consider two potential cybersecurity threats: a data breach and a denial-of-service (DoS) attack. A qualitative assessment might label both as “high risk,” but a probabilistic approach could reveal that the likelihood of a data breach is 15%, with a potential financial impact of $10 million, while the likelihood of a DoS attack is 5%, with a potential impact of $2 million. This quantitative insight allows the organization to prioritize its efforts on preventing data breaches, which pose a higher financial risk.
The NIST CSF 2.0’s existing framework can be augmented by incorporating these probabilistic assessments into the “Identify” and “Respond” Functions. Specifically, the “Risk Assessment” (ID.RA) Category can benefit from detailed probabilistic analysis, enabling organizations to map their risk profiles more accurately and allocate resources where they are most needed.
Ready to elevate your cybersecurity strategy with a data-driven approach?
Schedule a time with me to discuss your specific NIST CSF 2.0 risk assessment needs. I’ll provide tailored insights and professional recommendations on how a quantitative approach can give you clearer, more actionable results to strengthen your cybersecurity posture.
Informed Decision-Making for Cybersecurity Investments
Cybersecurity budgets are often constrained, and organizations must make tough decisions about where to invest. Probabilistic risk quantification provides the economic context needed to make these decisions more effectively. By understanding the potential financial impact of different risks, organizations can compare the cost of potential cybersecurity investments against the expected reduction in risk.
For example, if an organization faces a 20% chance of a ransomware attack with an expected loss of $5 million, the decision to invest $500,000 in advanced threat detection and response tools becomes easier to justify. The potential savings far outweigh the cost, making it a sound investment. This approach can be integrated into the “Protect” (PR) and “Detect” (DE) Functions of the NIST CSF 2.0, helping organizations evaluate the return on investment (ROI) for different cybersecurity initiatives.
Moreover, the “Govern” (GV) Function introduced in CSF 2.0 can be further strengthened by embedding risk quantification in governance practices. By quantifying risks, organizations can develop more precise cybersecurity policies, align them with broader business objectives, and ensure that they are adequately resourced.
Communicating Cyber Risk in Economic Terms
One of the challenges that cybersecurity professionals often face is effectively communicating the importance of cybersecurity to non-technical stakeholders, such as executives and board members. These stakeholders are typically more concerned with business outcomes and financial metrics than technical details.
Probabilistic risk quantification enables cybersecurity teams to translate technical risks into economic terms, making it easier to communicate their significance to the broader organization. For instance, instead of stating that there is a “high risk” of a cyberattack, a CISO could explain that there is a 25% chance of a cyber event occurring within the next year, which could result in losses of up to $7 million. This framing makes the risk more tangible and relatable to business leaders, helping to secure buy-in for necessary cybersecurity investments.
The Loss Exceedance Curve as shown in the illustration below is one example of how easy it is to quantify cyber-related risks.

The LEC curve can be dynamically updated with new information as it becomes available or used as a risk-modeling tool to compute the ROI on different investments.

The NIST CSF 2.0 framework already emphasizes the importance of communication in the “Respond” (RS) and “Recover” (RC) Functions, particularly in terms of incident response and recovery plans. Integrating probabilistic risk quantification into these areas can enhance an organization’s ability to convey the urgency and scale of potential risks, ensuring that cybersecurity remains a top priority at all levels of the organization.
Practical Examples of Probabilistic Risk Quantification
To illustrate the practical application of probabilistic risk quantification, consider the following examples:
- Scenario Analysis for Data Breaches: An organization might use probabilistic models to assess the likelihood and potential impact of a data breach based on industry trends, historical data, and threat intelligence. By simulating different scenarios (e.g., varying levels of data sensitivity, breach methods, and attack vectors), the organization can estimate the expected financial losses and identify the most cost-effective security controls to mitigate these risks.
- Monte Carlo Simulations for Investment Decisions: Before investing in a new security solution, an organization could perform a Monte Carlo simulation to model the potential outcomes of different investment strategies. This technique allows the organization to explore a wide range of scenarios and determine the probability distribution of potential returns, helping to guide investment decisions based on expected value rather than intuition alone. The LEC curves shown above are examples of Monte Carlo Simulations.
- Quantifying Supply Chain Risks: With supply chain attacks on the rise, organizations can use probabilistic risk quantification to assess the risks posed by third-party vendors. By analyzing the likelihood of a supply chain compromise and the potential downstream effects, organizations can prioritize their monitoring efforts and allocate resources to the most critical areas.
Conclusion
The integration of probabilistic risk quantification into the NIST CSF 2.0 framework offers a powerful enhancement that can help organizations better manage their cybersecurity risks. By providing a more precise understanding of risk, enabling more informed investment decisions, and facilitating clearer communication of cyber risk in economic terms, probabilistic risk quantification can significantly increase the effectiveness and applicability of the NIST CSF 2.0 framework.
As organizations continue to navigate an increasingly complex and hostile cyber environment, the adoption of advanced risk quantification techniques will become essential for maintaining resilience and securing the trust of stakeholders. By enhancing the NIST CSF 2.0 framework with these capabilities, organizations can ensure that their cybersecurity efforts are not only effective but also strategically aligned with their overall business objectives.
You can connect with me on LinkedIn and join my professional network.
I share weekly insights on quantifying cyber risk in dollars, not colors — including Monte Carlo simulation, loss exceedance modeling, Cyber Value at Risk (VaR), and NIST CSF quantification. If you’re an executive, CISO, or security leader looking for practical, data-driven approaches to cyber risk, let’s connect on LinkedIn.
Ready to elevate your cybersecurity strategy with a data-driven approach?
Schedule a time with me to discuss your specific NIST CSF 2.0 risk assessment needs. I’ll provide tailored insights and professional recommendations on how a quantitative approach can give you clearer, more actionable results to strengthen your cybersecurity posture.