CyberVaR 360™
Cyber Risk in Dollars, Not Colors

Cyber Risk in Dollars, Not Colors
Make board-ready decisions with CyberVaR 360™ — a quantitative risk modeling framework that transforms NIST CSF assessments into probability-based loss exposure you can measure, manage, and justify.
Unlock Cyber Risk in Dollars, Not Colors
Transform your NIST CSF assessments into clear, dollar-based insights with CyberVaR 360™ — our quantitative modeling framework that calculates breach probabilities, financial loss exposure, and ROI-backed investment priorities.
By combining Monte Carlo simulation, loss exceedance modeling, and Cyber Value at Risk (VaR), CyberVaR 360™ turns your current cybersecurity maturity and threat profile into actionable financial intelligence.
With these insights, your leadership team can:
- Quantify loss exposure across thousands of realistic breach scenarios
- Justify investments with clear ROI calculations
- Optimize cyber insurance coverage based on modeled losses
- Track cybersecurity maturity over time with data that boards and executives understand
All results are delivered in straightforward financial language, enabling executives, CISOs, and boards to prioritize resources, model risks, and communicate the potential impact of future events with clarity and confidence.
Latest Articles
-

The Business Case for Cyber Value at Risk (VaR) – Translating Threats into Dollars
Cyber Value at Risk (Cyber VaR) translates vague threat discussions into clear financial terms. Instead of relying on heatmaps or qualitative scores, executives can see their likely, average, and worst-case cyber losses—expressed in dollars. By applying proven financial risk methods like Monte Carlo simulation, Cyber VaR gives leaders visibility into tail risks, insurance gaps, and…
-

From Risk Matrices to Dollar-Based Insight: Why Business Leaders Must Quantify Cyber Risk
From heatmaps to finance: use loss-exceedance curves to buy down tail risk and brief the board in dollars, not colors.
-

5 Key Reasons Your Organization Should Implement NIST CSF 2.0 Profiles
In today’s financial and banking sectors, effective cybersecurity is critical to safeguarding sensitive data, maintaining trust, and ensuring compliance with regulatory standards. As cyber threats continue to evolve, business leaders must not only protect their organizations but also align cybersecurity efforts with broader business objectives. The NIST Cybersecurity Framework (CSF) 2.0 offers a robust approach…
-

Python for Newbs – A Learning Path to Begin Programming in Python
Python is a powerful, versatile, and easy-to-learn programming language that has gained immense popularity among developers, data scientists, and businesses alike. Known for its clean and readable syntax, Python is designed to be beginner-friendly while also being robust enough for advanced applications.
-

A Simple Fix for This Common Anaconda Problem
If you run a “conda list” command from your terminal or command window on your Mac or Windows PC and see an error that looks like the one shown below, there is a simple fix.
-

Step-by-Step Guide: Installing Anaconda on Mac and Windows and Writing a Simple “Hello Py” Project in Jupyter Notebook
In this article, I will walk you through the process of installing Anaconda on both Mac and Windows, setting up your environment, and writing a simple “Hello Py” project in a Jupyter Notebook.
-

Cybersecurity Threats vs. Risks: What’s the Difference and Why It Matters
The concepts of “threats” and “risks” are fundamental to cybersecurity and are defined by both NIST (National Institute of Standards and Technology) and ISO/IEC (International Organization for Standardization/International Electrotechnical Commission) in slightly different but complementary ways.
-

AI-Driven Cyber Risk Management: Leveraging Bayesian Networks in Cybersecurity for Business Leaders
In the rapidly evolving landscape of cybersecurity, businesses face increasingly complex and dynamic threats. The traditional methods of risk management and decision-making are being challenged by the need for more adaptive, intelligent, and data-driven approaches. Enter Bayesian Networks, a powerful form of Artificial Intelligence (AI) that can significantly enhance your organization’s ability to identify, assess,…
-

NIST CSF 2.0 Pre-Assessment Checklist
In the modern digital landscape, cybersecurity has become a cornerstone of risk management for organizations across all industries. As cyber threats evolve, so must the frameworks and strategies organizations use to protect their assets.
-

Cybersecurity as a Boardroom Priority: Engaging the C-Suite in Risk Management with NIST CSF
In today’s rapidly evolving digital landscape, cybersecurity is no longer just a technical issue relegated to IT departments—it’s a critical component of business strategy that requires the attention and engagement of the entire C-suite and board of directors.
-
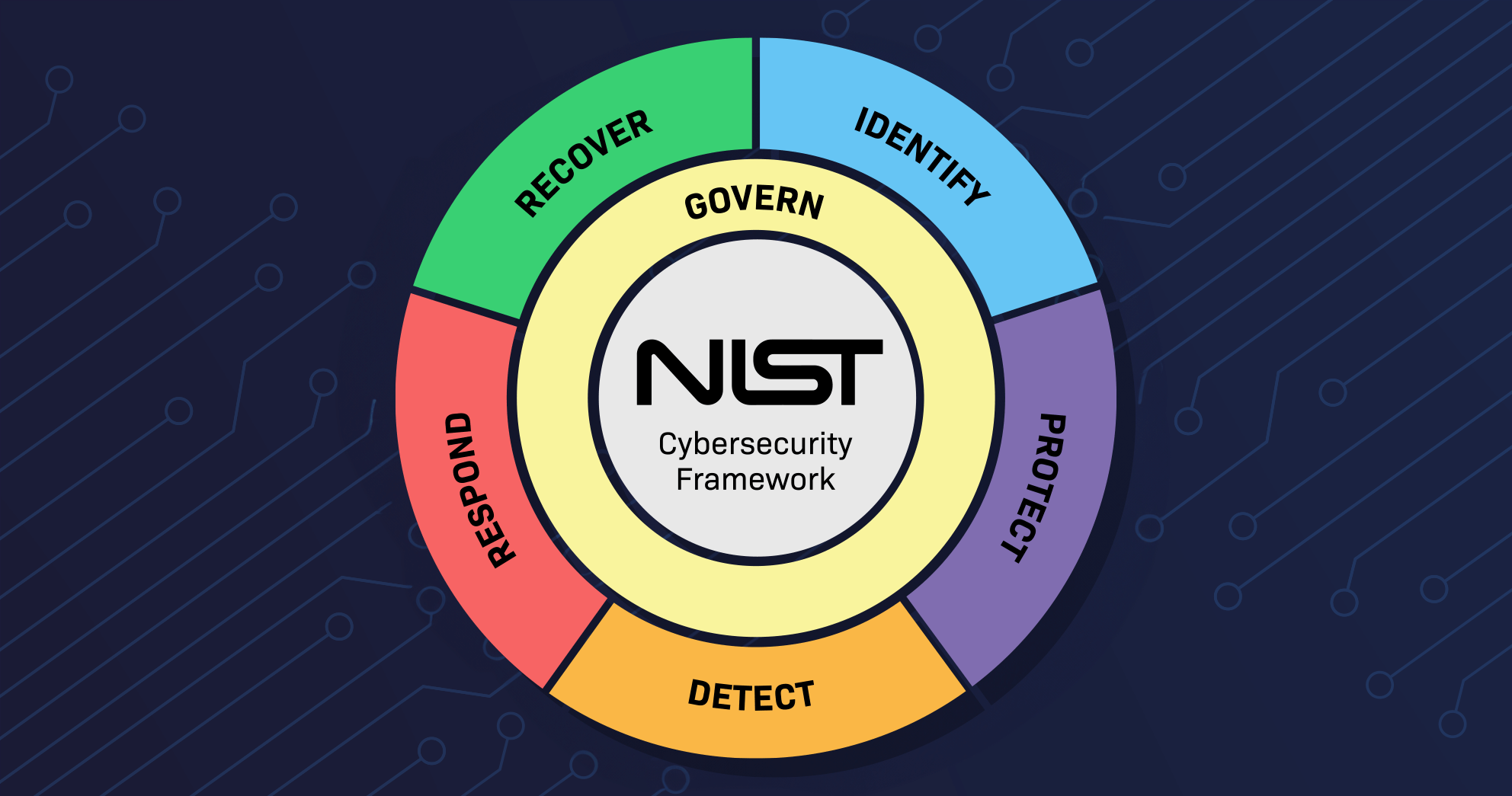
A Step-by-Step Guide to Implementing Organizational Profiles in NIST CSF 2.0
The NIST Cybersecurity Framework (CSF) 2.0 introduces several enhancements to help organizations manage their cybersecurity risks better. One of the most significant updates is the refined approach to Organizational Profiles. These Profiles are essential for understanding an organization’s cybersecurity posture, setting target objectives, and tracking progress over time. This step-by-step guide will walk you through…
-

Understanding and Communicating Cybersecurity Posture: The Value of NIST CSF 2.0
For senior business leaders, grasping the intricacies of cybersecurity might seem daunting, yet it is increasingly vital in today’s digital landscape. The NIST Cybersecurity Framework (CSF), now updated to version 2.0, offers a robust and flexible tool for understanding and communicating your organization’s cybersecurity posture. This framework is not just a technical resource; it is…
-

The Evolution of Cyber Risk Analysis: From The Risk Matrix to Bayesian Statistics
In the rapidly changing world of cybersecurity, the methods we use to assess and manage risk must evolve to keep pace with emerging threats. Traditional risk analysis methods, such as the risk matrix, have long been staples in the cybersecurity toolkit. However, as the complexity of cyber threats grows, these methods can fall short, offering…
-

Real-World Applications of Bayes’ Theorem in Cybersecurity
As the field of cybersecurity continues to grow in complexity, professionals are seeking more sophisticated methods to predict, prevent, and respond to cyber threats. Among the various tools at their disposal, Bayes’ Theorem stands out as a particularly powerful and versatile approach.
-

Why Bayes’ Theorem is a Game-Changer for Cybersecurity Risk Analysis
In the ever-evolving landscape of cybersecurity, where new threats emerge daily, and the stakes are higher than ever, organizations need more than just reactive strategies to protect their assets. They need a robust, data-driven approach to anticipate and mitigate risks before they manifest into serious breaches. This is where Bayes’ Theorem comes into play—a powerful…
-

Machine Learning vs. Bayesian Statistics in Python for Cybersecurity Risk Analysis
In this article, I explore the advantages and applications of two powerful analytical approaches: Machine Learning (ML) and Bayesian statistics in Python. Both methodologies have their unique strengths and are suited to different types of problems.
-

Estimating Phishing Email Frequency with the Poisson Distribution in Python: A Practical Guide for Cybersecurity Risk Assessment
In today’s article, I will show you how to use the Poisson distribution to estimate the number of phishing emails your organization receives per day. Understanding the frequency of these phishing attempts can help you adjust your incident response planning measures accordingly.
-
Analyzing Cybersecurity Risks: Estimating Phishing Attack Probabilities with Bayesian Statistics in Python Using Beta Distribution
In today’s digital landscape, cybersecurity threats are a significant concern for businesses of all sizes. Phishing attacks, where malicious actors attempt to deceive employees into revealing sensitive information or clicking on harmful links, are particularly prevalent.
-

Understanding Models for AI and Machine Learning
As artificial intelligence (AI) continues to evolve and permeate various aspects of our lives, understanding the foundational elements that make these technologies work is crucial. One of the core components of AI and machine learning (ML) systems is the model.
-

Most Common Python Libraries for Modeling with Distributions in Cybersecurity Risk Analysis
Python is an essential tool for cybersecurity professionals, offering powerful libraries for modeling distributions and conducting risk analysis. This article explores some of the most common Python libraries best suited for these tasks, explaining why each is an excellent choice for cybersecurity risk analysis.
-

Assessing the Risk and Impact of Phishing Attacks: A Step-by-Step Framework for Using Quantitative and Causal Methods
Phishing attacks pose a significant threat to organizations, leading to financial losses, data breaches, and reputational damage. Accurately assessing the risk and impact of phishing attacks is crucial for developing effective cybersecurity strategies.
-

Mobile Privacy Landscape
In an era of ubiquitous communication technology, the privacy of mobile phone users continues to be a significant privacy and security concern.
-

Are Tech Giants Apple and Google Bypassing VPNs With The Baseband Modem?
Theoretical Risks of VPN Bypass by Smartphone Manufacturers In the modern digital age, concerns about mobile privacy and data security are at the forefront of consumer technology discussions, particularly regarding the devices and software we use daily. One of the more alarming possibilities is that major smartphone manufacturers like Apple and Google could theoretically bypass…
-

The Business Case For Cyber Risk Automation
As digital threats like phishing attacks become increasingly sophisticated, traditional cybersecurity frameworks such as NIST CSF and ISO 27001/2 struggle to keep pace. While these frameworks are effective for meeting compliance requirements, they lack the dynamic adaptability to effectively manage new and evolving cybersecurity threats. This foundational approach is thus insufficient for today’s fast-paced cyber…